Page 1 of 1
SSL/TLS Client Test
Posted: 2019-07-15, 10:57
by Sampei Nihira
I removed the insecure cipher suites from my Firefox-based browsers.
I also applied this change to Chrome-based browsers.
I have practically no problems.
Only one website of the many I use is unattainable.
https://browserleaks.com/ssl
https://www.ssllabs.com/ssltest/viewMyClient.html
Re: SSL/TLS Client Test
Posted: 2019-07-15, 12:09
by Moonchild
What is your point in relation to Pale Moon?
Re: SSL/TLS Client Test
Posted: 2019-07-15, 16:17
by Sampei Nihira
Even Pale Moon maintains some insecure cipher suites, highlighted in the tests, which can be fixed.
Re: SSL/TLS Client Test
Posted: 2019-07-15, 16:21
by Isengrim
Which ciphers are listed as insecure by these tests?
(I cannot run these tests myself at the moment.)
Re: SSL/TLS Client Test
Posted: 2019-07-15, 16:36
by Sampei Nihira
See the difference between Chrome (insecure ciphers fixed) and Edge:
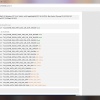
Re: SSL/TLS Client Test
Posted: 2019-07-15, 16:41
by Moonchild
There's 2 things at work here:
- These tests will mark all "CBC" ciphers as "weak" because there have been several attacks against this class of ciphers. IMHO this is both generalizing and incorrect. They are not weak ciphers just because they have a -potential- of getting more of a similar class of attacks launched against them (each of which was easily countered), and even more so they are not insecure. Note that insecure ciphers in Qualys' interface will be marked as such (in red and with the term INSECURE, for e.g. RC4).
In addition, they mark ciphers with a SHA-1 HMAC as "weak" which is actually kind of silly. While SHA-1 might not be strong enough for signatures, there is no problem using it for HMAC.
HMAC can be secure even when the underlying hash function is not collision resistant.
Intuitively, it makes sense that HMAC is secure as a MAC even with SHA-1, because a MAC does not allow a collision search. The only way to find the key would be to compromise the preimage resistance of SHA-1. HMAC in turn prevents length extension attacks and the like that would allow a forgery without knowing the key.
As an aside, even HMAC-MD5 hasn't been broken.
- The browser is a web client, which must maintain the broadest acceptable collection of cipher suites to prevent connectivity issues with sites that have "less than perfect" (according to the security community) scores for their https setups. While you personally might not have run into sites that would break by disabling all CBC ciphers, there are plenty of them out there. Unless the cipher suites involved become actually insecure (and not just "weak") or involving an unacceptable risk for secure connections, they should not be disabled by default in a client.
Re: SSL/TLS Client Test
Posted: 2019-07-16, 15:26
by Sampei Nihira
I thank you for your considerations.
With Pale Moon I prefer to eliminate weak/insecure ciphers.
With Chrome-based browsers it is easy to launch the browser without my modification.
You only need to run the browser without the relevant Command Line Switche.
Only this website of those I use does not work:
https://www.ilsoftware.it/
I wrote to the webmaster but he doesn't intend to change anything soon.
No problems on other websites including your forum.

Re: SSL/TLS Client Test
Posted: 2019-07-16, 16:36
by New Tobin Paradigm
Then you're a fool.
Re: SSL/TLS Client Test
Posted: 2019-07-17, 01:48
by Moonchild
https://www.ssllabs.com/ssltest/analyze ... oftware.it
ssl labs gives that site good marks ("
A") and there's nothing wrong with the server configuration. Suites with forward secrecy preferred (and using a very strong elliptic curve profile at that), TLS 1.2 support, not vulnerable to any of the "poodle" attacks, etc.
I have to agree with Tobin that you're being foolish for blindly disabling cipher suites in the browser just because you see "weak" marked alongside it which I already explained is being overzealous, and then using a different browser with generally less security-aware defaults for the sites that use still perfectly acceptable settings.
Re: SSL/TLS Client Test
Posted: 2019-07-17, 18:44
by Sampei Nihira
I know well that the website is secure.
Not only do I know the Director, but I have worked with him in the past on safety issues.
For the judgment of fool, in Italy there is a proverb that reads:
"The ox says horned to the donkey"
to say that one sees the defects only in others.
In fact I have not expressed opinions after the recent events that have affected your forum.
Your job is to express your point of view.
And let others follow their convictions respecting their free will.
Don't judge if you don't want to be judged.
Re: SSL/TLS Client Test
Posted: 2019-07-18, 07:37
by John connor
Wouldn't be prudent to trust the Dev of the browser you use on this forum than your own understanding?
Re: SSL/TLS Client Test
Posted: 2019-07-18, 08:35
by Utnapishtim
Sampei Nihira wrote: ↑2019-07-17, 18:44
I know well that the website is secure.
Not only do I know the Director, but I have worked with him in the past on safety issues.
Huh?

The point of using strong ciphers is to prevent decryption and impersonation by third parties. Whether you trust the owner's code has no bearing on it. That's like saying that if you send cash by mail, the postal workers will never steal it if the recipient is an honest and safety-aware person.
Re: SSL/TLS Client Test
Posted: 2019-07-18, 11:06
by Moonchild
Off-topic:Sampei Nihira wrote: ↑2019-07-17, 18:44
to say that one sees the defects only in others.
In fact I have not expressed opinions after the recent events that have affected your forum.
Your job is to express your point of view.
And let others follow their convictions respecting their free will.
"my" forum is also "your" forum. My "job" is to provide a browser, and -maybe- help with support for it. It's not to express opinions on fora.
If you're wanting to turn this around as somehow being oblivious to my own faults then you should realize that sometimes advice is just that: advice given by someone who has knowledge -- and not an "opinion".
Also, what "recent events" you may be alluding to: if you have issues with the community, then you should remind yourself you are here of your own volition, and it'd be yours to make peace with and solve.
But, I'll be happy to stop providing advice to you; makes my "job" of "
providing opinions" less work.

