Remote security exploit in all 2008+ Intel platforms
-
dark_moon
 Remote security exploit in all 2008+ Intel platforms
Remote security exploit in all 2008+ Intel platforms
We all know Intel ME is a big risk, but it is even worse:
Every Intel platform from Nehalem to Kaby Lake has a remotely exploitable security hole.
https://semiaccurate.com/2017/05/01/rem ... platforms/
Are you affected?
Every Intel platform from Nehalem to Kaby Lake has a remotely exploitable security hole.
https://semiaccurate.com/2017/05/01/rem ... platforms/
Are you affected?
-
wyMnNHXB
Re: Remote security exploit in all 2008+ Intel platforms
This article is strange - all "WE KNEW WE WARNED IT IS HAPPENING" and no details except basic ME descriptions from Wikipedia.
-
Fedor2
Re: Remote security exploit in all 2008+ Intel platforms
There is exploid indeed, and intel confirmed it too.
But what about that article pursue, to hype and scare people nothing else.
Is if only a one user here who using that intel technology?
But what about that article pursue, to hype and scare people nothing else.
Is if only a one user here who using that intel technology?
Re: Remote security exploit in all 2008+ Intel platforms
Pretty sure my Intel Celeron features this exploit as well.
With Pale Moon by my side, surfing the web is quite enjoyable and takes my headaches away! 
God is not punishing you, He is preparing you. Trust His plan, not your pain. #TrentShelton #RehabTime
God is not punishing you, He is preparing you. Trust His plan, not your pain. #TrentShelton #RehabTime
Re: Remote security exploit in all 2008+ Intel platforms
This vulnerability does not exist on Intel-based consumer PCs.
An unprivileged network attacker could gain system privileges to provisioned Intel manageability SKUs: Intel® Active Management Technology (AMT) and Intel® Standard Manageability (ISM).
In short: This applies only to provisioned PCs with specific management features enabled in the hardware. Specifically, these are the vPro processors that have been provisioned with the tech enabled already.An unprivileged local attacker could provision manageability features gaining unprivileged network or local system privileges on Intel manageability SKUs
https://communities.intel.com/docs/DOC-5693
If you don't have this, then you're not vulnerable.
Even if you do, you're not vulnerable over the network unless this has specifically been enabled and has been exploited by either the provisioner or an attacker with physical access to your PC.
Steps to check and resolve are in intel's advisory:
https://security-center.intel.com/advis ... geid=en-fr
"Sometimes, the best way to get what you want is to be a good person." -- Louis Rossmann
"Seek wisdom, not knowledge. Knowledge is of the past; wisdom is of the future." -- Native American proverb
"Linux makes everything difficult." -- Lyceus Anubite
"Seek wisdom, not knowledge. Knowledge is of the past; wisdom is of the future." -- Native American proverb
"Linux makes everything difficult." -- Lyceus Anubite
Re: Remote security exploit in all 2008+ Intel platforms
Pretty sure it doesn't. Is your Celeron a consumer PC? then no. Is it a vPro CPU? No? then you're not vulnerable. Yes? Then you're only vulnerable if your non-consumer PC came provisioned with remote management features enabled (which requires both setup and activation) AND you have a vulnerable firmware.LimboSlam wrote:Pretty sure my Intel Celeron features this exploit as well.
"Sometimes, the best way to get what you want is to be a good person." -- Louis Rossmann
"Seek wisdom, not knowledge. Knowledge is of the past; wisdom is of the future." -- Native American proverb
"Linux makes everything difficult." -- Lyceus Anubite
"Seek wisdom, not knowledge. Knowledge is of the past; wisdom is of the future." -- Native American proverb
"Linux makes everything difficult." -- Lyceus Anubite
Re: Remote security exploit in all 2008+ Intel platforms
Well, my donated desktop is not a consumer PC. It was originally used in a business/corporate office. However, the remote management features have been disabled. And the firmware is about 8-10 years old. It's running Windows 7 SP1 x64.
Anyway, I talked to my bro who gave it to me and he says I not to worry about it. Also, I might just get refurbish and resell it.
Anyway, I talked to my bro who gave it to me and he says I not to worry about it. Also, I might just get refurbish and resell it.
With Pale Moon by my side, surfing the web is quite enjoyable and takes my headaches away! 
God is not punishing you, He is preparing you. Trust His plan, not your pain. #TrentShelton #RehabTime
God is not punishing you, He is preparing you. Trust His plan, not your pain. #TrentShelton #RehabTime
-
dark_moon
Re: Remote security exploit in all 2008+ Intel platforms
The Intel remote vulnerability is much, much worse than you thought
https://www.privateinternetaccess.com/b ... e-thought/
In order to get administrator privileges to the server memory, all you needed to do was to submit a blank password field instead of the expected privileged-access password hash, and you would have unlimited and unlogged access to the entire server memory.
https://www.privateinternetaccess.com/b ... e-thought/
In order to get administrator privileges to the server memory, all you needed to do was to submit a blank password field instead of the expected privileged-access password hash, and you would have unlimited and unlogged access to the entire server memory.
Re: Remote security exploit in all 2008+ Intel platforms
Well, that Vulnerability Discovery Tool didn't do me much good, as it obviously requires Intel's ME drivers to be installed, in order to work:
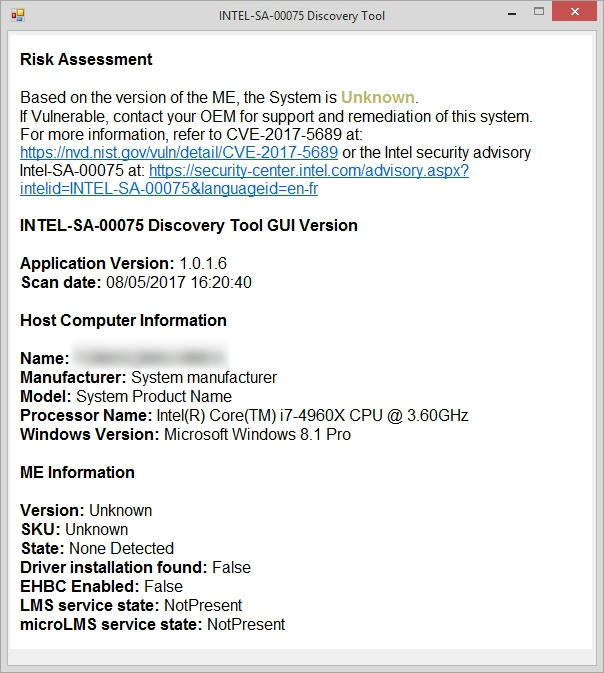
I've never installed that stuff, as I don't have any use for it.
In fact, I've always had the ME feature disabled on a user level in Device Manager, where it's called something as cryptic as "PCI Simple Communications Controller".
Anyway, if the security advisories issued by Intel indeed are correct, I guess I'm in the clear.

I've never installed that stuff, as I don't have any use for it.
In fact, I've always had the ME feature disabled on a user level in Device Manager, where it's called something as cryptic as "PCI Simple Communications Controller".
Anyway, if the security advisories issued by Intel indeed are correct, I guess I'm in the clear.
Re: Remote security exploit in all 2008+ Intel platforms
Your CPU has no vPro capability according to Intel: http://ark.intel.com/products/77779/Int ... o-4_00-GHz
What 'board is it on?
EDIT: this results page should list all Intel CPUs with vPro: http://ark.intel.com/products/77779/Int ... o-4_00-GHz
What 'board is it on?
EDIT: this results page should list all Intel CPUs with vPro: http://ark.intel.com/products/77779/Int ... o-4_00-GHz
Re: Remote security exploit in all 2008+ Intel platforms
The motherboard is a 'Asus Rampage IV Black Edition'.satrow wrote:What 'board is it on?
It uses the Intel X79 chipset, which also lacks vPro support.
Re: Remote security exploit in all 2008+ Intel platforms
You should therefore be quite safe but check for and uninstall the AMT software and uninstall any Intel Management drivers from Device Manager - System devices should you wish to keep squeaky clean.
Tool on Majorgeeks to disable/clean out the AMT driver: http://www.majorgeeks.com/files/details ... l_amt.html
Tool on Majorgeeks to disable/clean out the AMT driver: http://www.majorgeeks.com/files/details ... l_amt.html
Re: Remote security exploit in all 2008+ Intel platforms
Like I pointed out in my post with the screenshot; I've never installed any of that crap.satrow wrote:check for and uninstall the AMT software and uninstall any Intel Management drivers from Device Manager
I've always had it disabled in Device Manager too.
Re: Remote security exploit in all 2008+ Intel platforms
Uninstall it from Device manager, cleaner, no reboot needed (if you're referring to the ME).
Re: Remote security exploit in all 2008+ Intel platforms
Whatever you uninstall from Device Manager will simply be re-detected at next boot up.satrow wrote:Uninstall it from Device manager, cleaner, no reboot needed (if you're referring to the ME).
You need to disable it!
Re: Remote security exploit in all 2008+ Intel platforms
On uninstall via DevMan, you should get a popup asking if you also want to delete the drivers, do so and it won't install again (in this instance, it shouldn't even leave an ! over the unknown device, it won't exist).


